Application elevation for non-administrative users
Despite whatever you may feel about UAC for use on your home PC, it is a great tool for desktops in the enterprise. “Run As” served its purpose well in the XP days almost a decade ago (has it really been that long?). As much as I like UAC in my enterprise for easy elevation of administrative tasks and accompanied profile virtualization, it’s not without its shortcomings. Namely, it is lacking the ability to selectively elevate specific applications that, for whatever reason, require administrative privileges, without the user knowing an administrator’s password. The solution used to be to grant the users administrative privileges outright or try to figure out the required permissions for every file write, registry call, or function the application would need to perform (subinACL). There has to be a better way. The principle of least privilege is a best practice that should be enforced in all environments, which serves to protect the organization as a whole as well as the individual user.
The problem:
I have several legacy applications with custom device drivers, built-in updaters, or program dependencies requiring change or write access to files that live in protected system directories. I don’t want the user to have to call for support every time they need to run the program and I don’t want to grant them administrative access.

- The Manager which contains the GPO editor extensions and RSOP snap-ins.
- The Client which is a kernel-mode driver that lives on the user's PC including group policy client side extension and WMI namespace (deployable via MSI)
The driver on the client PC watches processes launched locally and checks against any configured GPO rules. If a rule exists for a launched process, the driver elevates the security token for that process based on settings in the rule. The added value for this method is that when applications are elevated the file system is not virtualized as is the case with a default “run as admin” operation. Additional privileges are added to the user’s security token for that specific process when it’s launched. This is like adding the user to the Administrators group temporarily just for that process for the duration it’s run (sudo).
The Manager piece is installed on your domain controllers, very straight forward.

Once installed the new features are immediately available in GPMC. Create a new or edit an existing GPO. You will see a new settings container under both the computer and user sections of the policy called Computer Security and User Security, respectively.

Before you can get to creating new policy items you will have to configure licensing. Along with the new settings containers, you should see a new button between View and Help called Privilege Manager. Open the Licensing tool and you will see 3 tabs: Local, GPO, and Request. You can generate a new request from the tool or simply import and activate a license you have received. To enable you first have to import the license you have purchased, then deploy it to the GPO in which you have enabled Privilege Manager features.

Deployment is done via the GPO License tab.

Once the license is active you can begin setting up policies. There are a number of options at your disposal which at first glance look a lot like a software restriction policy.

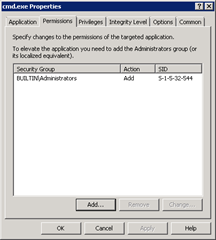
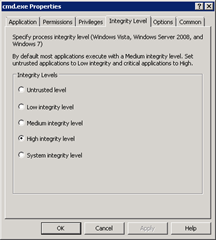
Once the program information is supplied you can assign permissions, privileges, and integrity settings to it. You can get very granular at each level if you need to.
Under the last tab, Common, you can apply filters to your policy much like a GPO Preference item.

Testing
To test, I have set up a path rule for cmd.exe that will elevate a non-administrative user to the builtin\administrators group for this process alone. The PowerBroker client can be deployed via GPO or other systems management solution to the specific PCs that need it. A single service will run on the client PCs called BeyondTrust Reporting Service. To prove that this solution works I will use a tool deployed with the client called Policy Monitor (polmon) as well as execute a privileged command from the prompt.
Logged into a PC with my test user John Doe, with PolMon running, I launch cmd.exe. Polmon displays that cmd.exe has been invoked and that there is a rule match for this application. The rule is parsed and John’s security token is elevated for the cmd process only, as configured.

With my elevated command prompt running, John executes a GPResult /R which under normal user mode only displays information about the user account. Computer related information is normally denied from being displayed without command prompt elevation. As you can see John was able to display RSOP results for both the user and computer accounts. Not only that the file system is not virtualized as you can see from the working directory. The user sees no UAC or other prompts, the application just works.

A quick note on licensing. PowerBroker:Desktops is licensed per enabled user that has the client installed. The license is installed at an OU level of your choosing and enabled per GPO. According to the documentation, each active user in an OU will be counted as a user for PowerBroker. So as far as the software is concerned any user in an OU that it can see is considered an active user. BeyondTrust has a few ways to deal with this, both extremely fair. You can use an enterprise license, enabling access for all users, which requires an annual true-up where you prove the actual number of users using the product. The other option is buying x number of licenses and they will provide some additional license padding for growth. User licenses will run in the $30-40 range each so depending on the size of your environment is very reasonable.
But here's the rub...BeyondTrust will only issue you a temporary 30-day license until their invoice is paid. Yep, even if you buy through the channel! So if your reseller (their partner) doesn't pay their invoice, guess what? No permanent license for you. If your reseller (their partner) has net 60 terms with them, guess what, no permanent license for you. This is an extremely paranoid way to license a product that I have honestly not seen ever in over a decade in this business! I am over 60 days now, on my second temp license, and am still waiting for my permanent lic. The product definitely works but their licensing policy is asinine. Buyer beware!
PowerBroker:Desktops is an extremely clean solution that works exactly as advertised. For those of us that have to deal with badly written or legacy applications requiring administrative access, this solution is a winner. I have ~20 users that will need this functionality so at the quoted price point this solution is a great deal with the amount of time and frustration it will save.











No comments: